Is how to tell if someone is accessing your iphone remotely someone secretly accessing your iPhone without your knowledge? In today’s digital age, protecting our devices from remote access is more important than ever. Your iPhone contains sensitive information and personal data that you wouldn’t want falling into the wrong hands. Stay ahead of potential threats by learning how to detect if someone is remotely accessing your device and what steps you can take to secure it. Let’s dive in!
The Importance of Protecting Your iPhone
Your iPhone is more than just a phone – it’s a treasure trove of personal information. From photos and messages to banking details and social media accounts, your device holds a wealth of sensitive data that should be kept secure at all times.
In the wrong hands, unauthorized access to your iPhone can lead to identity theft, financial loss, and privacy breaches. Remote access allows cybercriminals to spy on you, track your location, read your messages, and even listen in on calls without your knowledge.
Protecting your iPhone goes beyond setting a passcode; it requires vigilance against potential threats like hacking attempts or malware infections. By staying informed about security best practices and taking proactive measures to safeguard your device, you can minimize the risk of unauthorized access and keep your personal data safe from prying eyes.
Signs That Your iPhone May be Accessed Remotely
Have you ever had that unsettling feeling that someone might be accessing your iPhone without your knowledge? It’s important to stay vigilant and look out for signs that your device may be compromised.
One potential red flag is noticing strange activity on your phone, such as apps opening or closing on their own, messages being sent without your input, or unfamiliar accounts logged into. Keep an eye out for any unusual behavior that you can’t explain.
Another indicator of remote access is a sudden decrease in battery life or data usage. If you notice a significant change in these metrics without any obvious reason, it could be a sign that someone else is using your device behind the scenes.
Additionally, if you experience unexplained crashes, freezes, or sluggish performance on your iPhone, it could indicate unauthorized access. These issues may stem from malicious software running in the background without your knowledge.
Possible Reasons for Remote Access to Your iPhone
Have you ever wondered why someone would want to access your iPhone remotely? There could be various reasons behind this invasive act. One possible reason is for malicious intent, such as stealing personal information or financial data stored on your device. Hackers may target iPhones to gain access to sensitive information that can be exploited for fraudulent activities.
Another reason could be espionage or spying. Individuals or organizations may attempt to remotely access an iPhone to monitor the user’s activities, track their location, or eavesdrop on conversations through the microphone. This type of remote access is concerning and a violation of privacy rights.
Furthermore, some individuals might try to access your iPhone remotely out of curiosity or simply for fun. They may want to see what apps you have installed, read your messages, or view your photos without permission. Regardless of the motive, unauthorized remote access to your iPhone is unacceptable and must be prevented at all costs.
It’s essential to stay vigilant and take necessary precautions to protect your device from potential threats related to remote access.
Steps to Secure Your iPhone from Remote Access
Securing your iPhone from remote access is crucial in today’s digital age. To start, always ensure your device has the latest software updates installed. These updates often include security patches that help protect against potential vulnerabilities.
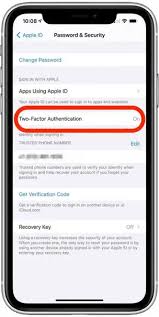
Another important step is to enable two-factor authentication for your Apple ID. This adds an extra layer of security by requiring a verification code in addition to your password when signing in on a new device.
Regularly reviewing and managing the apps that have access to your data can also help prevent unauthorized access. Be cautious when granting permissions to third-party apps and revoke access if necessary.
Moreover, setting a strong passcode or using Touch ID/Face ID for unlocking your device adds an additional level of protection. Avoid sharing sensitive how to tell if someone is accessing your iphone remotely information over unsecured networks and consider using a VPN for added security while browsing.
By taking these proactive steps, you can significantly reduce the risk of unauthorized remote access to your iPhone and safeguard your personal data effectively!
Prevention Tips to Keep Your iPhone Safe
To keep your iPhone safe from remote access, it’s crucial to stay vigilant and implement preventive measures. One of the most effective ways to protect your device is by setting up a strong passcode or using biometric authentication like Face ID or Touch ID. These security features add an extra layer of protection and make it harder for unauthorized individuals to gain access.
Regularly updating your iPhone’s operating system how to tell if someone is accessing your iphone remotely and apps is another essential step in safeguarding your device against potential vulnerabilities that could be exploited by hackers. Software updates often include security patches that help prevent remote how to tell if someone is accessing your iphone remotely access attacks.
Avoid connecting to unsecured Wi-Fi networks, as they can be breeding grounds for cyber threats. Instead, opt for trusted networks or use a virtual private network (VPN) when accessing the internet on-the-go. Additionally, be cautious when downloading apps from third-party sources, as they may contain malware designed to compromise your device’s security.
Enabling two-factor authentication (2FA) adds an extra layer of security by requiring a secondary verification method before granting access to your accounts. This prevents unauthorized users from remotely accessing sensitive information stored on your iPhone. Remember, staying proactive and informed about cybersecurity best practices is key to keeping your digital life secure.
Conclusion
Protecting your iPhone from remote access is crucial in safeguarding your personal information and privacy. By being aware of the signs that someone may be accessing your device remotely and taking proactive steps to secure it, you can minimize the risk of unauthorized access. Remember to regularly update your software, use strong passwords, enable two-factor authentication, and avoid connecting to unsecured networks. Stay vigilant and prioritize the security of your iPhone to keep your data safe from potential intruders.
 Time News Global Business, Technology, Entrepreneurship News
Time News Global Business, Technology, Entrepreneurship News